Web-based attacks could create chaos in the physical world

Computer security researchers suggest ways to thwart new form of cybercrime
Most experts on computer crime focus on attacks against Web servers, bank account tampering and other mischief confined to the digital world. But by using little more than a Web search engine and some simple software, a computer-savvy criminal or terrorist could easily leap beyond the boundaries of cyberspace to wreak havoc in the physical world, a team of Internet security researchers has concluded.
At a recent Association for Computing Machinery conference on privacy in an electronic society, the researchers — including a Johns Hopkins faculty member — described how automated order forms on the Web could be exploited to send tens of thousands of unwanted catalogs to a business or an individual. Such an onslaught would not only pose problems for the victim, but it could also paralyze the local post office charged with making such deliveries, the researchers suggested. After explaining how such attacks could take place, the researchers proposed several technological “fixes” that could help prevent them.
The rapid growth of the World Wide Web has enabled many merchants, government agencies and non-profit organizations to make sales catalogs and information packets available to anyone who can fill out a simple on-line form. But these forms, the researchers say, have also opened a gateway that could allow disruptive activity to spill out of cyberspace. “People have not considered how easily someone could leverage the scale and automation of the Internet to inflict damage on real-world processes,” said Avi Rubin, technical director of the Information Security Institute at The Johns Hopkins University and one of the authors of the paper.
Rubin and two other researchers first determined that a popular search engine such as Google could be used to locate online order forms. They also discovered that simple software could be launched to automatically recognize and fill in fields such as “name,” “address” and “city,” and then submit the catalog request online. “It could be set up to send 30,000 different catalogs to one person or 30,000 copies of one catalog to 30,000 different recipients,” said Rubin. “This could create a great expense for the sender, a huge burden for local postal facilities and chaos in the mail room of a business targeted to receive this flood of materials.”
The technique could also be used to exploit the increasingly common Web-based forms used to request repair service, deliveries or parcel pickups, said Rubin, who also is an associate professor in the Department of Computer Science at Johns Hopkins. Tracking down the attacker could be difficult, he added. The offender could easily escape detection by loading the program onto a floppy disk or a small USB hard disk and paying cash for a few minutes of time at an Internet café. By the time the damage was discovered, the culprit would have vanished, Rubin said.
Because of the confusion and costs such attacks could inflict, Rubin and his fellow researchers wondered whether they should make public the technological weakness they’d uncovered; by doing so, they might provide a “blueprint” for people to launch such attacks. With this in mind, they did not publish their paper for some time after the initial research was done. However, after a popular search engine introduced its new Application Programming Interfaces, the researchers concluded that the attacks they envisioned were now much more likely to occur. In their paper they stated that “there is also a risk in not disclosing vulnerabilities for which there are known solutions. By not educating people who are in a position to defend against an attack, it can be more damaging to bury knowledge of a vulnerability than to announce it.”
The researchers suggested several methods to deter the attacks they described. One is to set up online forms so that they cannot easily be picked up by a search engine. Another is to alter the HTML coding used to create an online form so that it no longer contains easily recognizable field names such as “name” and “address.” (Such coding changes would not be visible to the person filling out the form.)
Yet another option is to include in each form a step that must be completed by a human computer user. This process, called a Reverse Turing Test, could display writing that could not easily be recognized by a computer, or it could require some other visual task that would trip up an automated ordering program. Other deterrents suggested by the researchers include client puzzles and monitored systems called “Honeypots,” which are set up to attract cyber-attackers for early detections.
Hoping to prevent the type of cyber-attacks they’ve envisioned, the researchers have conferred with a top technology administrator from the U.S. Postal Service and have made their concerns and recommendations public on the Web. “To prevent these damaging activities,” Rubin said, “we need to look at the interface between cyberspace and the real world and to make sure there is a real person submitting a legitimate request, not a computer program launching a disruptive attack.”
Media Contact
All latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles
High-energy-density aqueous battery based on halogen multi-electron transfer
Traditional non-aqueous lithium-ion batteries have a high energy density, but their safety is compromised due to the flammable organic electrolytes they utilize. Aqueous batteries use water as the solvent for…

First-ever combined heart pump and pig kidney transplant
…gives new hope to patient with terminal illness. Surgeons at NYU Langone Health performed the first-ever combined mechanical heart pump and gene-edited pig kidney transplant surgery in a 54-year-old woman…
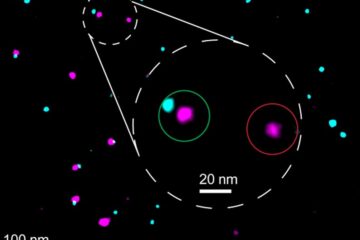
Biophysics: Testing how well biomarkers work
LMU researchers have developed a method to determine how reliably target proteins can be labeled using super-resolution fluorescence microscopy. Modern microscopy techniques make it possible to examine the inner workings…





















