New marking process traces spammers, pirates and hackers

Penn State researchers have proposed a new marking process for Internet messages to make it easier to trace the originators of spam, illegal copyrighted material or a virus attack.
The new marking scheme produced less than one percent false positives per 1000 attacking addresses in simulated distributed denial of service attacks and even fewer false positives and zero missed detections tracing addresses transferring copyrighted material in another simulation.
Marking messages via the Penn State approach involves no more loss of privacy than that of a postmark. Ihab Hamadeh, doctoral candidate in computer science and engineering, and Dr. George Kesidis, associate professor of electrical engineering and of computer science and engineering, developed the process.
“The technique offers internet access providers a real-time, cost-effective way to conduct forensics and improve security for the Internet,” Kesidis says. “In addition, the approach will be demonstrably effective during an incremental deployment phase, thereby, creating incentives for broader deployment to satisfy the cyber security concerns of the Internet services industry and government regulators.”
To defend against spam and viruses or to stop illegal file sharing, an organization must be able to identify the originator of the offending messages. However, spammers, pirates and hackers most often use incorrect, disguised or false addresses on their messages or data packets to deter trace back. Such spoofed addresses are illegal in the U.S. but so far, effective.
To overcome such spoofed source addresses, the Penn State researchers propose a strategy in which every message or data packet is marked with an identifying number by a border router. Border routers are peripheral stations that a packet passes through on its way onto the Internet.
Since every packet is forwarded onto the Internet and marked by only one trustworthy border router, spoofers would not be able to insert false marks on their packets to undermine trace back. The packets would always be traceable to a specific border router and could be stopped or investigated at that point.
While other researchers have proposed marking packets, the Penn State approach is the first to use border routers to mark packets. The marks are intended to occupy obsolete fields in the IP packet headers and are formed from the 32-bit IP addresses of the border router.
If the available obsolete field in the IP packet header is less than 32 bits long, the Penn Staters propose segmenting the border router’s IP address into several overlapping fragments that can fit. Each such fragment would be used as a possible mark by the router.
At the victim’s side, fragments from packets identified as malicious are pieced together to form the addresses of the border routers that marked and forwarded them. The overlapping fields allow the victim to correlate fragments from the same border router thereby reducing false positives.
The researchers have described their approach in two papers presented last year: “Packet Marking for Traceback of Illegal Content Distribution” and “Performance of IP Address Fragmentation Strategies for DDoS Traceback.”
The University has filed an invention disclosure and is patenting the process. The research was supported, in part, by a Cisco Ltd University Research Project grant.
Media Contact
More Information:
http://www.psu.edu/All latest news from the category: Communications Media
Engineering and research-driven innovations in the field of communications are addressed here, in addition to business developments in the field of media-wide communications.
innovations-report offers informative reports and articles related to interactive media, media management, digital television, E-business, online advertising and information and communications technologies.
Newest articles
High-energy-density aqueous battery based on halogen multi-electron transfer
Traditional non-aqueous lithium-ion batteries have a high energy density, but their safety is compromised due to the flammable organic electrolytes they utilize. Aqueous batteries use water as the solvent for…

First-ever combined heart pump and pig kidney transplant
…gives new hope to patient with terminal illness. Surgeons at NYU Langone Health performed the first-ever combined mechanical heart pump and gene-edited pig kidney transplant surgery in a 54-year-old woman…
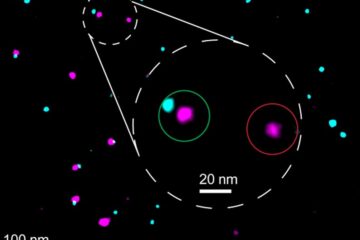
Biophysics: Testing how well biomarkers work
LMU researchers have developed a method to determine how reliably target proteins can be labeled using super-resolution fluorescence microscopy. Modern microscopy techniques make it possible to examine the inner workings…





















