Managing your identity

Privacy is a huge concern to many citizens, customers, patients, internet users and telephone subscribers especially as the lines are being blurred between professional and private lives.
However, many people are simply unaware of just how much of their personal data is being stored and processed, whether that is in the form of cookie trails that track their internet usage, video from surveillance systems, such as Closed Circuit Television (CCTV), or the purchases they make using credit cards and company loyalty cards.
Marit Hansen is the Deputy Privacy Commissioner of the Data Protection Authority (DPA) of Schleswig-Holstein, Germany and suggests that while the processing of personal data has become a part of everyday life in today's information society, this means that privacy is increasingly under threat. She suggests that conventional approaches to privacy have intensified the problem because these systems store personal and private data, such as your name and address, date of birth, mother's maiden name, and credit details online.
Hansen believes that a user-controlled approach to information management is the only way to solve the problem by allowing individuals to manage their privacy. This approach would allow individuals to create “partial identities” that separated personal data depending on the specific context and allowed the website, healthcare worker, or other interested party access only to the limited data they needed.
“User-controlled identity management systems are not a panacea for all privacy problems, but they can act as a gateway and guardian for individual privacy,” explains Hansen. As such, such an approach has the potential to become a key tool for future privacy concepts.
In related work, also published this month in the IJIPM, Ronald Leenes of the Tilburg Institute for Law, Technology, and Society in The Netherlands, says user-centric identity management as an indispensable tool for privacy protection.
Leenes believes that not only is our information privacy being compromised but it is “under siege on the internet.” He suggests that a person's digital persona can be used for good in the context obtaining personalised services on the internet, for instance, for bad when that persona is used to discriminate against a particular individual.
There are insufficient legal controls in place, Leenes, says, to allow internet users to control their privacy, which means that new infrastructure on the web must be implemented, based on the aforementioned user-controlled identity management, that allows individuals to control the data they are sharing with websites.
Media Contact
More Information:
http://www.inderscience.comAll latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles
High-energy-density aqueous battery based on halogen multi-electron transfer
Traditional non-aqueous lithium-ion batteries have a high energy density, but their safety is compromised due to the flammable organic electrolytes they utilize. Aqueous batteries use water as the solvent for…

First-ever combined heart pump and pig kidney transplant
…gives new hope to patient with terminal illness. Surgeons at NYU Langone Health performed the first-ever combined mechanical heart pump and gene-edited pig kidney transplant surgery in a 54-year-old woman…
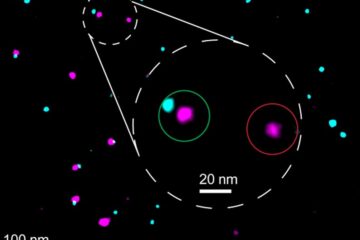
Biophysics: Testing how well biomarkers work
LMU researchers have developed a method to determine how reliably target proteins can be labeled using super-resolution fluorescence microscopy. Modern microscopy techniques make it possible to examine the inner workings…





















