How we are tricked into into giving away our personal information

Since it is difficult to change people’s behavior, it doesn’t help to provide training about how to behave securely. This is shown by Marcus Nohlberg in his dissertation at Stockholm University in Sweden in which he studied attacks that are called social engineering in IT contexts.
The concept of social engineering refers to the art of using social codes and knowledge of human behavior to get us to provide information or do things we should not do. A topical example happened very recently in Sweden, where people received calls from a person who purported to represent the IT office at their bank and asked them to identify themselves using their personal bank encoders. The attacker then used these codes to steal money from the victims’ accounts.
“I predicted a couple of years ago that this kind of attack would become common, especially account fraud,” says Marcus Nohlberg.
Despite the serious consequences, with many successful fraud attempts, this technique has received little attention among researchers. Marcus Nohlberg’s research has led to enhanced knowledge about what methods attackers use and what it is that makes people and organizations so vulnerable. Somewhat depressingly, Marcus Nohlberg’s research shows that information and training do not work as well as we think:
“There will always be a small group of people who do not do as they were taught. What’s more, it’s all too seldom that people undergo training in security issues in general. To change behavior, this is something that needs to be worked with constantly. The best thing is practical training, and it’s probable that organizations will need to start running internal checks where they in fact create fictitious attacks in order to identify weaknesses,” says Marcus Nohlberg.
Social engineering as a method of fraud is costly for the attacker since it requires commitment and time. However, software and technologies already exist that can interact with other people automatically:
“You can easily imagine how serious it will be when such programs target victims via digital forums like Facebook in the future. When it becomes just as simple as spreading spam, this will present a major threat to social activities on the Internet.”
In his research, Marcus Nohlberg presents a description of fraud crimes from the perspectives of victims, perpetrators, and defenders, but he also offers suggested measures for preventing attacks, based on his own experiences from controlled attacks.
Title of dissertation: Securing Information Assets — Understanding, Measuring and Protecting against Social Engineering Attacks.
Media Contact
More Information:
http://www.su.seAll latest news from the category: Social Sciences
This area deals with the latest developments in the field of empirical and theoretical research as it relates to the structure and function of institutes and systems, their social interdependence and how such systems interact with individual behavior processes.
innovations-report offers informative reports and articles related to the social sciences field including demographic developments, family and career issues, geriatric research, conflict research, generational studies and criminology research.
Newest articles
A universal framework for spatial biology
SpatialData is a freely accessible tool to unify and integrate data from different omics technologies accounting for spatial information, which can provide holistic insights into health and disease. Biological processes…

How complex biological processes arise
A $20 million grant from the U.S. National Science Foundation (NSF) will support the establishment and operation of the National Synthesis Center for Emergence in the Molecular and Cellular Sciences (NCEMS) at…
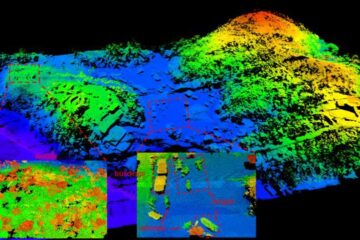
Airborne single-photon lidar system achieves high-resolution 3D imaging
Compact, low-power system opens doors for photon-efficient drone and satellite-based environmental monitoring and mapping. Researchers have developed a compact and lightweight single-photon airborne lidar system that can acquire high-resolution 3D…





















