Passwords to guard entry aren’t enough to protect complex data

Security mechanisms also must protect what goes out
Passwords to guard entry aren’t enough to protect complex data – security mechanisms also must protect what goes out
“Data can easily find itself in danger of being accessed by ’bad guys,’” says emeritus professor of computer science Gio Wiederhold, who will speak about trusted information databases Feb. 14 in Seattle at the annual meeting of the American Association for the Advancement of Science (AAAS). “Passwords and other means of access control are okay, but additional security mechanisms are needed to provide security.” To ensure that data records are not released into the wrong hands, Wiederhold suggests adding filters to outgoing data.
Traditional security systems often utilize access control in which passwords are the key to identifying authorized users and granting them access to data. While doctors or nurses may have access to medical data in a hospital database, they cannot access financial data in the hospital’s accounting database. Conversely, an insurance company can access financial records but not patient medical records. Patients, in contrast, can request access to both types of data. A database administrator in a traditional system defines different roles for different users, and those roles define the type of access allowed.
The good news about traditional systems is that bad guys must employ multiple ’hacks’ to get past the firewalls, operating systems and the database security itself. The bad news is that because the filter is at the level of user access, security stops once a user gains access to material authorized for his or her role. If a good guy turns bad – as in the case where a disgruntled employee with access privileges decides to do some damage – the database becomes endangered.
A severe disadvantage to the access-driven security model is that it requires that all of the contents be well organized and placed into neat bins for access by those with authorized roles. Protection is poor for data that are complex, multipurpose, unstructured, formatted as images, or now used for roles not recognized when the data were first collected. Medical records, for instance, are nearly impossible to organize for all the roles that they serve.
The most serious issue is that access control does not consider collaboration. For instance, in a medical setting, many types of users legitimately need access to patient data, and their legitimate access rights intersect in many ways. A document given to a researcher in a specific area, say cardiac disease, may also include information about pregnancy, psychological profile, or HIV status. Because of their holistic role, patient medical records cannot be organized to separate all of those aspects. Simply removing patient identification from every separate aspect of a patient’s record disables research, since long-term follow-up and integration of data from encounters at diverse sites are needed. Wiederhold says filters can and should check outgoing documents for terms warranting more protection.
“When these [medical] and other databases are designed, the possible uses and security needs cannot be fully considered,” Wiederhold says. If a company outsources work to a consultant, the consultant needs access to the company database. By using release control – which monitors the contents of documents being delivered to the requestor – alongside traditional access control, the consultant is restricted to material that is relevant to a particular project, Wiederhold says. The databases need not be redesigned to reclassify or remove data that is inappropriate or proprietary.
Protecting data before it gets released means vetting the contents of documents retrieved from internal files, Wiederhold says. Document release protection may be desirable for diverse systems with data output, such as e-mail, file systems, databases and websites. Such filters are already operational in e-mail systems employing “dirty word” filters and in military systems that “fuzzify” shared data that only can be seen clearly using specially supplied equipment.
As data increase in complexity, it becomes increasingly difficult to define a good security model that works well for different types of collaborating users. For example, customers of an online file-sharing business need to be able to access files from the company’s database, but they should not be able to see contents pertaining to other customers, such as credit card numbers or e-mail-address. Recognizing that we must allow access to many types of users – each with their own objectives and ethics – means that a simple good guy/bad guy access model is inadequate. While access control working alongside release control will improve the protection of privacy, complex security definitions may conflict with each other or even form security holes, Wiederhold says. “The scope of potential use of data is so large that no approach that relies on any specific data organization will be adequate for all future needs,” he says. “But relying only on access control is certainly inadequate.”
CONTACT: Dawn Levy, News Service: (650) 725-1944, dawnlevy@stanford.edu
COMMENT: Gio Wiederhold, Computer Science: (650) 725-8363, gio@cs.stanford.edu
Media Contact
More Information:
http://www.stanford.edu/dept/news/All latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles
A universal framework for spatial biology
SpatialData is a freely accessible tool to unify and integrate data from different omics technologies accounting for spatial information, which can provide holistic insights into health and disease. Biological processes…

How complex biological processes arise
A $20 million grant from the U.S. National Science Foundation (NSF) will support the establishment and operation of the National Synthesis Center for Emergence in the Molecular and Cellular Sciences (NCEMS) at…
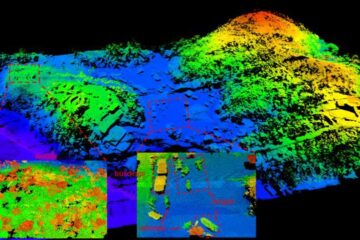
Airborne single-photon lidar system achieves high-resolution 3D imaging
Compact, low-power system opens doors for photon-efficient drone and satellite-based environmental monitoring and mapping. Researchers have developed a compact and lightweight single-photon airborne lidar system that can acquire high-resolution 3D…





















