Intruder Alert: Method Provides Double Computer Crime-Solving Evidence

Like an episode of “CSI: Computers,” a UF researcher has developed a technique that gives digital detectives twice the forensic evidence they now have to catch all kinds of hackers, from curious teenagers to disgruntled employees to agents of foreign governments.
Writing in the current issue of the International Journal of Digital Evidence, UF doctoral student Mark Foster proposes a new and improved method of computer crime solving, called “process forensics.” “If a guy walks into a bank and robs it, leaving footprints behind or his fingerprints on the counter, the forensic analyst would come in and find those traces of what happened,” said Foster. In the same way, process forensics merges two existing types of digital evidence – intrusion-detection and checkpointing technology – to give an investigator the most possible information to crack a case, said Foster, a computer science and engineering student conducting the research for his dissertation with UF professor of computer science Joseph Wilson, who co-wrote the paper. “If you detect the intruder – or even if you’re just suspicious that an intruder’s around – you start creating checkpoints,” Foster said. “And then later, those checkpoints will serve to give us some forensics.”
Checkpoints are essentially periodic snapshots of a running computer program, or process. Programmers use them as a safety backup – if the power goes out while a program is still running, they can return to the most recent checkpoint rather than starting over from the beginning.
Many current programs don’t have built-in checkpointing technology, creating more work for programmers, Foster said. So he developed a technique that automatically creates checkpoints within a program. After working separately on computer security and intrusion-detection software, he realized that combining checkpoints with intrusion detection would create an efficient forensics tool, he said. “If the photographs are taken at the right times, then we can see how they got in, what was tampered with,” Foster said.
Foster targets intruders who want to break into systems that are host-based – or centrally located in one primary computer, which is then linked to numerous satellite workstations. “You can have a scenario where user Bob – he’s malicious, he’s tired of class, and he wants to try to mess with everybody. In a multiuser environment, you’ve got to have boundaries set up and once you have those, somebody wants to come along and get through them.”
One way for an evil-minded hacker to break into a host-based computer system is to sneak in through a “hole,” a flaw in a running program the hacker can exploit to take control of the program, run his own programs or generally gum up the works, Foster said. This type of attack is called a buffer overflow attack, he said.
Current intrusion-detection software helps an investigator find out if someone has broken into a system, identifies the intruder and prevents future attacks. However, the software first has to learn the computer system well enough to detect anything out of the ordinary, such as unexpected changes to files and suspicious programs. Detection also can require more steps, such as additional software, modification of current software or preparing a program ahead of time for monitoring.
Foster’s process-forensics method also includes an intrusion-detection system that improves on current software by streamlining detection and eliminating the training phase. “This is definitely an area that is up-and-coming in forensics,” said John Leeson, an associate professor of computer science at the University of Central Florida and an editor of the International Journal of Digital Evidence. “I like the fact that he’s taking a proactive approach – forensics for years has been a reactive field.
“The idea is that you kind of need to know when something is happening before you start collecting information, or it’ll be a lot of useless information,” Leeson said. “Mark’s proposing a tool that could be activated by an automatic intrusion-detection system. I think that’s going to definitely enhance the value of digital forensics, to be able to deal with incidents as they are occurring.”
Computer forensics is a broad field. “A lot of times it’s recovering deleted files or looking for hidden files,” Foster said. “You have a child stalker who’s on the Internet stalking children, and they track him down, they confiscate his computer, and they say to the forensic guy, ’What kind of evidence can you get from his computer?’”
Foster said his method targets a different kind of computer abuse – intruders who want to hijack a running program. ”This is definitely kind of a different angle than the traditional stuff,” he said.
Media Contact
More Information:
http://www.ufl.eduAll latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles
A universal framework for spatial biology
SpatialData is a freely accessible tool to unify and integrate data from different omics technologies accounting for spatial information, which can provide holistic insights into health and disease. Biological processes…

How complex biological processes arise
A $20 million grant from the U.S. National Science Foundation (NSF) will support the establishment and operation of the National Synthesis Center for Emergence in the Molecular and Cellular Sciences (NCEMS) at…
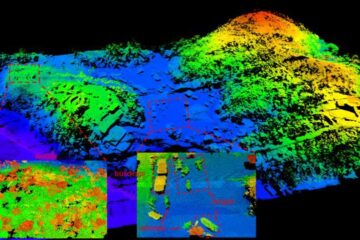
Airborne single-photon lidar system achieves high-resolution 3D imaging
Compact, low-power system opens doors for photon-efficient drone and satellite-based environmental monitoring and mapping. Researchers have developed a compact and lightweight single-photon airborne lidar system that can acquire high-resolution 3D…





















