Advances in Computer Network Intrusion Detection

Researchers from Oxford University’s Computing Laboratory have developed techniques to spot malicious attacks on computer networks, that include the use of Inductive Logic Programming (ILP) techniques to automatically determine the semantics of novel attack strategies.
Intrusions often take place where there are vulnerabilities within computer systems. For example, one of the most common of these is the buffer overflow, where an attacker sends overly long transactions to a server. The aim is to overflow the server’s buffer with code that runs automatically, allowing the attacker to execute malicious commands via the network.
A recent example was the “Code Red” worm released on Friday 13th July 2001. The attack caused havoc for programmes running on Microsoft Internet Information Server and slowed down Internet traffic considerably. No one was able to stop it automatically; few recognised what strategy the attack was using and system administrators had to look for it manually in the registers of their systems.
Existing [firewall and security] systems try to detect malicious transactions by comparing the signatures of known attacks. However, attackers can simply change subtle parameters in their attack, without altering the strategy they are using, and easily thwart such systems. Importantly, few technologies have been implemented to detect broad classes of attack strategies or to automatically generate detection strategies by learning from novel attacks.
Code Red proved that self-replicating attacks are dangerous and that systems are vulnerable. Current detection methods based on attack signatures rely on the manual analysis of registers and logs and are ineffective in the long term.
The semantic intrusion detection system developed at Oxford uses general rules rather than signatures to determine whether transactions are attempting to use a known attack strategy. Furthermore, such general rules can be generated from examples of attack attempts using the technology of ILP. An ILP system relies on knowledge represented as sets of general rules which are used explain new examples of intrusions and little interaction is required once this knowledge has been imparted.
Oxford University’s technology transfer company, Isis Innovation, has filed a UK patent application on the principles behind this invention and is interested to hear from companies that wish to license this technology for further development.
Media Contact
More Information:
http://www.isis-innovation.comAll latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles
A universal framework for spatial biology
SpatialData is a freely accessible tool to unify and integrate data from different omics technologies accounting for spatial information, which can provide holistic insights into health and disease. Biological processes…

How complex biological processes arise
A $20 million grant from the U.S. National Science Foundation (NSF) will support the establishment and operation of the National Synthesis Center for Emergence in the Molecular and Cellular Sciences (NCEMS) at…
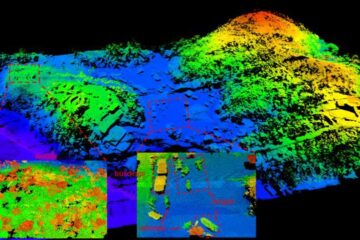
Airborne single-photon lidar system achieves high-resolution 3D imaging
Compact, low-power system opens doors for photon-efficient drone and satellite-based environmental monitoring and mapping. Researchers have developed a compact and lightweight single-photon airborne lidar system that can acquire high-resolution 3D…





















