The Information Security Dictionary — a compendium about the terms of IT-Security

Defining over 1,200 of the most commonly used words in the security field
The newly released Information Security Dictionary (1st Edition) (published by Springer Science) offers information security experts, systems analysts, policy makers, managers and students a reference tool to find the most commonly used terms in the field. The dictionary defines these terms in easy to understand language, provides more detail in Tables and easy cross-referencing leading the reader to related terms if need be.
Details about the book:
Gattiker, Urs E. (2004) The Information Security Dictionary Defining the Terms that Define Security for E-Business, Internet, Information and Wireless Technology Series : The Kluwer International Series in Engineering and Computer Science (Springer Science – Foundations of Computing , Vol. 767. ISBN: 1-4020-7927-3. Available at bookstores near you, online booksellers and from the publisher at: www.springeronline.com/sgw/cda/frontpage/0,,5-156-22-33310929-0,00.html
The dictionary is published both in electronic and printed form, thereby offering users easy online searches as well as finding the terms online. As Professor Urs E. Gattiker (Ph.D.) from the security portal CASEScontact reported, the idea of the dictionary was based on his experience attending various security conferences that often neither panel members nor the audience were always sure about the terminology being discussed.
In contrast to established disciplines, information security experts have the challenge to work in a rapidly developing field that has yet to find a shared vocabulary. In turn, it is often difficult for experts and users alike to be sure that one understands certain concepts fully without referring to a reference document. The Information Security Dictionary is a handy tool that provides one with the definitions of over 1,200 items most often used by system administrators, software engineers and security experts. What makes the dictionary especially helpful is it being:
* concise,
* providing help for non-technical users, as well as
* depth for experts (e.g., different types of worms, viruses, hacking attacks are defined), and
* links and references to related terms (e.g., virus and worms
How Does it Work?
The Information Security Dictionary is published both in electronic as well as a hardover printed version. The electronic version provides for easy online searching while the hardcover copy can be used in one’s reference library. Besides providing the reader with information about related terms so additional information is easily found, the dictionary offers the reader extensive appendices providing links and information to:
* glossaries and news information regarding cybersecurity,
* tools and software sites enabling one to better protect critical systems,
* information about new regulation regarding e-commerce, privacy, and telecommunication,
* standards, and
* newsletters, alerts and skill development tools and tricks regarding information security.
The Information Security Dictionary focuses on concepts rather than implementation.
Quotes
“IT security is a newly emerging discipline that is of utmost importance in a world, where we are becoming ever more dependent on information that is being transported and/or stored on: residential computers, including notebooks and personal digital assistants (PDA), in data warehouses and also a country’s critical infrastructure. Unfortunately, it is sometimes difficult to keep track of new terminology or have two experts agree on how to define the problem. This further complicates matters for users and decision-makers alike. The Dictionary tries to reduce this confusion and bring in a bit of order” said Urs E. Gattiker, Professor for Management and Information Sciences at ISNM.
“The Information Security Dictionary is based on our need for reducing complexity by sharing a vocabulary that facilitates communicating about a complex matter, while helping to better protect critical infrastructure and information.”
“Often it is difficult for an educated reader to understand journal articles or books dealing with security issues because it is unclear how the author may have defined certain terminology ” states Gattiker, Professor for Management and Information Sciences at ISNM and director of CASEScontact in Germany. “But a system administrator trying to convince top management of the need for additional vigilance regarding security needs to be able to explain basic terminology to an audience that is focusing on the bottom line. This is where the Information Security Dictionary comes in.”
Media Contact
More Information:
http://security.weburb.dk/frame/show/news/3408All latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles
A universal framework for spatial biology
SpatialData is a freely accessible tool to unify and integrate data from different omics technologies accounting for spatial information, which can provide holistic insights into health and disease. Biological processes…

How complex biological processes arise
A $20 million grant from the U.S. National Science Foundation (NSF) will support the establishment and operation of the National Synthesis Center for Emergence in the Molecular and Cellular Sciences (NCEMS) at…
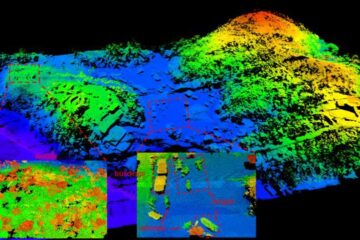
Airborne single-photon lidar system achieves high-resolution 3D imaging
Compact, low-power system opens doors for photon-efficient drone and satellite-based environmental monitoring and mapping. Researchers have developed a compact and lightweight single-photon airborne lidar system that can acquire high-resolution 3D…





















