New Technique Targets C Code to Spot, Contain Malware Attacks

Root exploits take over the system administration functions of an operating system, such as Android. A successful Android root exploit effectively gives hackers unfettered control of a user’s smartphone.
The new security tool is called Practical Root Exploit Containment (PREC). It refines an existing technique called anomaly detection, which compares the behavior of a downloaded smartphone application (or app), such as Angry Birds, with a database of how the application should be expected to behave.
When deviations from normal behavior are detected, PREC analyzes them to determine if they are malware or harmless “false positives.” If PREC determines that an app is attempting root exploit, it effectively contains the malicious code and prevents it from being executed.
“Anomaly detection isn’t new, and it has a problematic history of reporting a lot of false positives,” says Dr. Will Enck, an assistant professor of computer science at NC State and co-author of a paper on the work. “What sets our approach apart is that we are focusing solely on C code, which is what most – if not all – Android root exploits are written in.”
“Taking this approach has significantly driven down the number of false positives,” says Dr. Helen Gu, an associate professor of computer science at NC State and co-author of the paper. “This reduces disturbances for users and makes anomaly detection more practical.”
The researchers are hoping to work with app vendors, such as Google Play, to establish a database of normal app behavior.
Most app vendors screen their products for malware, but malware programmers have developed techniques for avoiding detection – hiding the malware until users have downloaded the app and run it on their smartphones.
The NC State research team wants to take advantage of established vendor screening efforts to create a database of each app’s normal behavior. This could be done by having vendors incorporate PREC software into their app assessment processes. The software would take the app behavior data and create an external database, but would not otherwise affect the screening process.
“We have already implemented the PREC system and tested it on real Android devices,” Gu says. “We are now looking for industry partners to deploy PREC, so that we can protect Android users from root exploits.”
The paper, “PREC: Practical Root Exploit Containment for Android Devices,” will be presented at the Fourth ACM Conference on Data and Application Security and Privacy being held March 3-5 in San Antonio, Texas. Lead author of the paper is former NC State graduate student Tsung-Hsuan Ho. The paper was co-authored by Daniel Dean, a Ph.D. student in Gu’s lab at NC State.
The work was supported by the National Security Agency; U.S. Army Research Office grant W911NF-10-1-0273; National Science Foundation grants CNS-1149445, CNS-1253346, and CNS-1222680; IBM Faculty Awards and Google Research Awards.
-shipman-
Note to Editors: The paper abstract follows.
“PREC: Practical Root Exploit Containment for Android Devices”
Authors: Tsung-Hsuan Ho, Daniel J. Dean, Xiaohui Gu, and William Enck, North Carolina State University
Presented: March 3-5 at the Fourth ACM Conference on Data and Application Security and Privacy in San Antonio, Texas.
Abstract: Application markets such as the Google Play Store and the Apple App Store have become the de facto method of distributing software to mobile devices. While official markets dedicate significant resources to detecting malware, state-of-the-art malware detection can be easily circumvented using logic bombs or checks for an emulated environment. We present a Practical Root Exploit Containment (PREC) framework that protects users from such conditional malicious behavior. PREC can dynamically identify system calls from high-risk components (e.g., third-party native libraries) and execute those system calls within isolated threads. Hence, PREC can detect and stop root exploits with high accuracy while imposing low interference to benign applications. We have implemented PREC and evaluated our methodology on 140 most popular benign applications and 10 root exploit malicious applications. Our results show that PREC can successfully detect and stop all the tested malware while reducing the false alarm rates by more than one order of magnitude over traditional malware detection algorithms. PREC is light-weight, which makes it practical for runtime on-device root exploit detection and containment.
Media Contact
All latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles
A universal framework for spatial biology
SpatialData is a freely accessible tool to unify and integrate data from different omics technologies accounting for spatial information, which can provide holistic insights into health and disease. Biological processes…

How complex biological processes arise
A $20 million grant from the U.S. National Science Foundation (NSF) will support the establishment and operation of the National Synthesis Center for Emergence in the Molecular and Cellular Sciences (NCEMS) at…
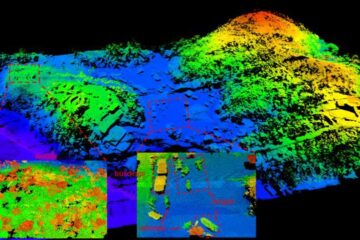
Airborne single-photon lidar system achieves high-resolution 3D imaging
Compact, low-power system opens doors for photon-efficient drone and satellite-based environmental monitoring and mapping. Researchers have developed a compact and lightweight single-photon airborne lidar system that can acquire high-resolution 3D…





















