To Detect Cyberattacks, New Software System Developed at UB Profiles ’Normal’ Computer Habits

An early version of a new software system developed by University at Buffalo researchers that detects cyberattacks while they are in progress by drawing highly personalized profiles of users has proven successful 94 percent of the time in simulated attacks.
The “user-level anomaly detection system” was described here today (Oct. 10, 2002) at the military communications conference known as MILCOM 2002.
“We have developed a new paradigm, proactively encapsulating user intent where you basically generate a profile for every single user in the system where security is a major concern,” said Shambhu Upadhyaya, Ph.D., associate professor of computer science and engineering at UB and co-author of the paper.
In addition to the paper presentation, MILCOM invited Upadhyaya to give a half-day tutorial on the new intrusion detection system at the meeting.
Upadhyaya directs UB’s Center of Excellence in Information Systems Assurance Research and Education, one of 36 in the U.S. chosen by the National Security Agency to develop new programs to conduct research and train students to protect the nation’s information technology systems from cyberterrorism.
The new UB intrusion detection system is being developed for application in highly secure facilities, such as those in the military.
“Existing approaches look at a past record of computer activity because those systems produce audits of activity for every user,” he explained. “Our methodology is a marriage of two known techniques: misuse and anomaly detection. We use an assertion/rule-based approach to precisely capture the initial bracket of activity and then fine-tune this profile to reflect ongoing activity, making highly personalized and accurate profiles possible.
“Also, since users are being constantly monitored, this system can detect intrusions or attacks on-the-fly.”
The UB system generates a user profile according to data about standard operations and commands that each user follows to carry out specific tasks.
The system is designed to detect significant deviations from procedures followed by normal users.
While some commercially available computer security packages already feature user-profiling, Upadhyaya noted that they are based on “low-level” methods — meaning they seek out deviations on the basis of huge amounts of data, so they end up creating many false alarms.
“User modeling is computationally hard,” said Upadhyaya. “Since many of these existing systems treat this problem purely statistically, any deviation from the norm is signaled as an anomaly, but it is often the case that an intrusion has not occurred.
“It’s a nuisance because an alarm can go off as often as every five minutes,” he said.
By contrast, the system he developed with co-authors Rankumar Chinchani, a doctoral candidate in the UB Department of Computer Science and Engineering, and Kevin Kwiat of the Air Force Research Laboratory in Rome, N.Y., is based on the idea that the computation habits of normal users generally are well-defined and that he or she will work within those bounds.
“The normal behavior of computer users has been very well characterized,” said Upadhyaya. “Normal users stick within well-defined parameters. Intruders or hackers, on the other hand, will not be able to carry out their intended operations within such well-defined parameters, and so will make the scope of his or her activities overly permissive,” said Upadhyaya. “Our system is based on detecting that kind of behavior.”
The key to the UB system’s success and its “scalable” feature is that its monitoring system operates at a high level, examining commands that users execute to perform certain operations. This is in contrast to the low-level monitoring that many existing packages perform, which examine commands as basic as the ones and zeroes of which email messages are composed.
“Our system is looking for a sequence of operations that falls within certain ’normal’ parameters,” he explained.
“For example, if you want to make a document, you do certain things in a certain order, you create the document, you use a word processing program, you may run Spellcheck. Our system knows what to look for in the normal sequence that is necessary to accomplish this job. Any deviations from that are assumed to be potential cyberattacks.”
The work was funded by the Air Force Research Laboratory in Rome, N.Y.
Media Contact
More Information:
http://www.buffalo.edu/All latest news from the category: Information Technology
Here you can find a summary of innovations in the fields of information and data processing and up-to-date developments on IT equipment and hardware.
This area covers topics such as IT services, IT architectures, IT management and telecommunications.
Newest articles

Why getting in touch with our ‘gerbil brain’ could help machines listen better
Macquarie University researchers have debunked a 75-year-old theory about how humans determine where sounds are coming from, and it could unlock the secret to creating a next generation of more…
Attosecond core-level spectroscopy reveals real-time molecular dynamics
Chemical reactions are complex mechanisms. Many different dynamical processes are involved, affecting both the electrons and the nucleus of the present atoms. Very often the strongly coupled electron and nuclear…
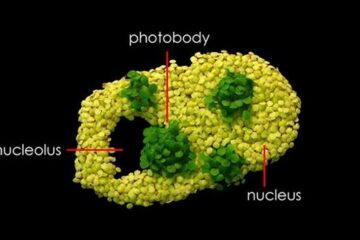
Free-forming organelles help plants adapt to climate change
Scientists uncover how plants “see” shades of light, temperature. Plants’ ability to sense light and temperature, and their ability to adapt to climate change, hinges on free-forming structures in their…





















