RFID chips in car keys and gas pump pay tags carry security risks

Thieves could exploit encryption vulnerabilities, computer scientists warn
A popular radio-frequency ID system that is used to deter car thefts and as a convenience device for the purchase of gasoline can be defeated with low-cost technology, computer scientists from The Johns Hopkins University and RSA Laboratories have determined.
Their findings, described in a new research paper, indicate that the encryption in RFID microchips in some newer car keys and wireless payment tags may not keep thieves at bay. Using a relatively inexpensive electronic device, criminals could wirelessly probe a car key tag or payment tag in close proximity, and then use the information obtained from the probe to crack the secret cryptographic key on the tag, the scientists said. By obtaining this key, lawbreakers could more easily circumvent the auto theft prevention system in that person’s car or potentially charge their own gasoline purchases to the tag owner’s account.
The researchers uncovered the vulnerability while studying the Texas Instruments Registration and Identification System, a low-power radio-frequency security system used worldwide. The researchers said that more than 150 million of these transponders are embedded in keys for newer vehicles built by at least three leading manufacturers. The transponders are also inside more than 6 million key chain tags used for wireless gasoline purchases. The computer security researchers discovered a way that tech-savvy thieves can get around the encryption safeguards in these systems.
The research paper has been posted online at: http://rfid-analysis.org/
“We’ve found that the security measures built into these devices are inadequate,” said Avi Rubin, technical director of the Johns Hopkins Information Security Institute and an author of the study. “Millions of tags that are currently in use by consumers have an encryption function that can be cracked without requiring direct contact. An attacker who cracks the secret key in an RFID tag can then bypass security measures and fool tag readers in cars or at gas stations.”
“In cars as in commerce, RFID is becoming a lynchpin for security in day-to-day life,” said Ari Juels, principal research scientist of RSA Laboratories. “It is important that RFID devices offer a level of security commensurate with the value of the assets they protect. Our aim is to help the industry achieve this standard.”
The radio-frequency ID system studied by the research team was designed to thwart car thieves, provide fast and convenient contactless payments and safeguard wireless transactions. In vehicles, it uses a passive, unpowered transponder chip embedded in the key and a reader inside the car, connected to the fuel injection system. If the reader does not recognize the transponder, the car will not start, even if the physical key inserted in the ignition is the correct one. This innovation has greatly reduced auto theft. In the gasoline purchase system studied by the researchers, a reader inside the gas pump must recognize a small key-chain tag that is waved in front of it. Upon system approval, the transaction is then charged to the tag owner’s credit card.
Security verification takes place through a procedure called a challenge/response protocol. When the key or tag is nearby, the reader transmits a random string of ones and zeroes to it. The transponder in the key or tag then processes these numbers in a specific way and sends a numeric message back to the reader for authentication.
The researchers from Johns Hopkins and RSA Laboratories were able to unravel the mathematical process used in this verification. They then purchased a commercial microchip costing less than $200 and programmed it to find the secret key for a gasoline purchase tag owned by one of the researchers. By linking 16 such chips together, the group cracked the secret key in about 15 minutes. (In this system, an owner’s credit card information is not carried on the chip and is not revealed by breaking the pass’s security. In addition, this system possesses other security safeguards designed to protect customers from repeated fraudulent purchases made with a contactless device. The company that markets this system has said it has no knowledge that any fraudulent purchases have ever been made with a cloned version of its device.)
The researchers had similar success with a chip-equipped car key. With the secret key in hand, the team was able to simulate the RFID tag and disarm the car’s anti-theft system without the built-in tag present. (Keyless remote control systems to lock and unlock car doors do not use RFID chips).
The researchers alerted Texas Instruments, manufacturer of the radio frequency systems, about the security vulnerabilities they had detected and demonstrated them to Texas Instruments in the lab. The Johns Hopkins-RSA team recommended a program of distributing free metallic sheaths to cover its radio frequency devices when they are not being used. This could make it more difficult for thieves to electronically steal the secret keys in the tags when they were not in use.
The Texas Instruments system is only one of a number of RFID systems on the market. The Johns Hopkins-RSA team has also been examining another system, not produced by Texas Instruments, that uses an active, battery-powered transponder chip. The team expects to prepare a paper soon on that work.
Media Contact
All latest news from the category: Power and Electrical Engineering
This topic covers issues related to energy generation, conversion, transportation and consumption and how the industry is addressing the challenge of energy efficiency in general.
innovations-report provides in-depth and informative reports and articles on subjects ranging from wind energy, fuel cell technology, solar energy, geothermal energy, petroleum, gas, nuclear engineering, alternative energy and energy efficiency to fusion, hydrogen and superconductor technologies.
Newest articles
High-energy-density aqueous battery based on halogen multi-electron transfer
Traditional non-aqueous lithium-ion batteries have a high energy density, but their safety is compromised due to the flammable organic electrolytes they utilize. Aqueous batteries use water as the solvent for…

First-ever combined heart pump and pig kidney transplant
…gives new hope to patient with terminal illness. Surgeons at NYU Langone Health performed the first-ever combined mechanical heart pump and gene-edited pig kidney transplant surgery in a 54-year-old woman…
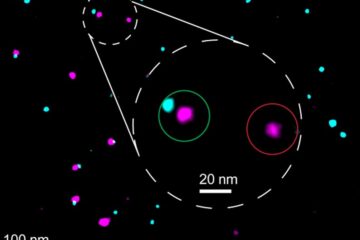
Biophysics: Testing how well biomarkers work
LMU researchers have developed a method to determine how reliably target proteins can be labeled using super-resolution fluorescence microscopy. Modern microscopy techniques make it possible to examine the inner workings…





















